PhD Candidate
University of Michigan, Ann Arbor, MI
Biography
Shibo Chen is a PhD Candidate of computer architecture at University of Michigan CELAB (Computer Engineering Lab) and ADA (Center for Applications Driving Architectures). His research interests include heterogeneous computation, datacenter architecture and agile hardware design. He is advised by Prof. Todd Austin.
I have lots of wise and interesting friends. Let’s visit one of them!
My website get visits from friends around the world! ( well, hopefully ;) )
Interests
- Heterogeneous Computation
- Datacenter Architecture
- Agile Hardware Design
Education
-
PhD in Computer Science and Engineering, 2024 (expected)
University of Michigan, Ann Arbor, MI
-
Graduate Certificate in Innovation & Entrepreneurship
University of Michigan, Ann Arbor, MI
-
BSc in Computer Science with High Distinction, 2019
University of Michigan, Ann Arbor, MI
Experience
Platform Architect Intern
Tenstorrent Inc.
Proposed and studied architecture changes that boost both multi-core performance and power efficiency.
Drafted testplan for cache and fabric verification.
Developed workflow for multi-core. multi-chiplet fabric traffic testing and simulation.
Configured Arteris IP for non-conherent traffic.
Platform Architect Intern
Tenstorrent Inc.
Developed in-house reconfigurable fabric performance model for heterogeneous multicore systems.
Designed configuration semantics to represent a wide range of farbric design options.
President and Social Chair
Computer Science & Engineering Graduate Students at UM
Publications
Projects
Shadowclone: Thwarting and Detecting DOP Attacks with Stack Layout Randomization and Canary
Control-flow hijacking attacks have been hard to deploy due to the widespread adoption of control-flow attack defenses such as Control-flow Integrity (CFI). This fact has led to a wide deployment of exploiting non-control data, which are not protected by CFI defenses. Non-control data attacks can be used to corrupt critical data or leak sensitive information. Furthermore, data-oriented programming (DOP) is able to achieve Turing-complete computation capabilities without leaving the control-flow graph of the programs. In this paper, we present a compile time stack layout randomization scheme- Shadowclone -to thwart and detect DOP attacks effectively. Shadowclone generates randomized clones of vulnerable target functions and randomly selects one copy of clones to execute during runtime. In addition, we also insert compile-time random canaries into stack variables and check its integrity before the function returns. In the evaluation section, we show that our approach can thwart and detect DOP attacks efficiently by limiting attacker’s success chance to less than 1%. Shadowclone also has low performance overhead when the program is small and has few function calls.
An Alpha-64 Out-of-Order Processor Design
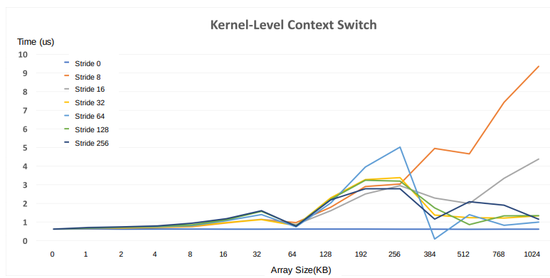
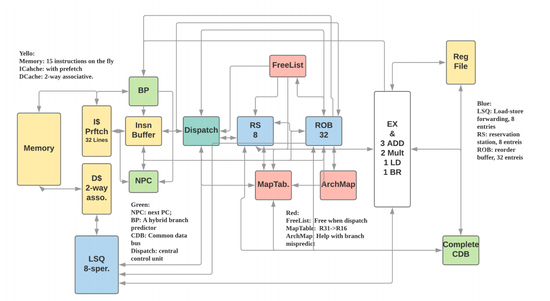
Our team implemented a three-way superscalar alpha-64 out-of-order CPU. We are able to achieve 100MHz and IPC of 0.94 with Synopsys 90nm generic library for education under the constraint area requirements.
ThundaTag: Disparate Domain Tagging to Enforce Benign Program Behavior
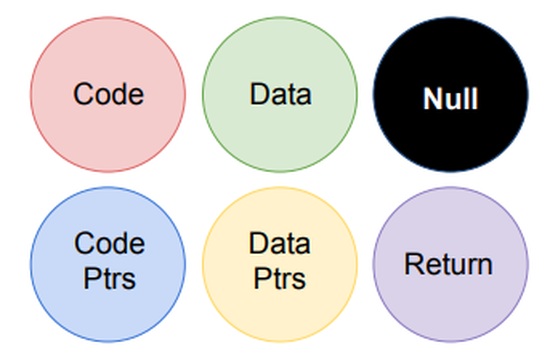
In this project, we implemented and evaluated the architectural support for domain tagging. Our study shows that such design only requires negligible area overhead and induces low performance overhead.
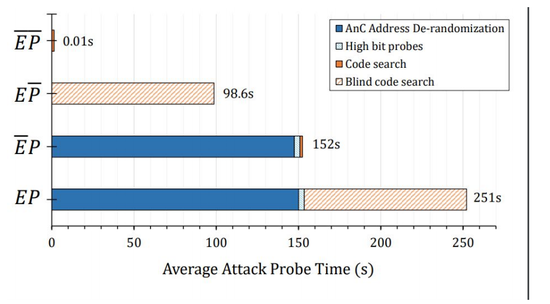
Understanding the Value of Ensemble of Moving Target Defenses in Morpheus
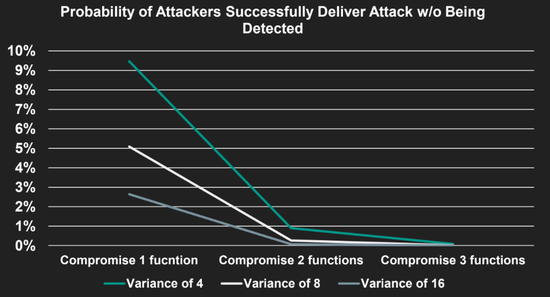
In this work, I studied the average time needed to penetrate a de-featured Morpheus design. The result underscores the robustness of Morpheus defenses.
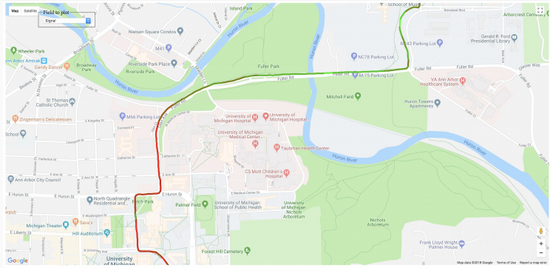
PowerSpy Upgraded: Location Tracking using Mobile Device Power Analysis
In this work, we extended the original Powerspy paper to more environments. Our study shows the availability of attacker using this attack to conduct indoor tracking.