START:UAVs
Software Techniques for Automated Resiliency and Trustworthiness in Uncrewed Aerial Vehicles
Software Techniques for Automated Resiliency and Trustworthiness in Uncrewed Aerial Vehicles
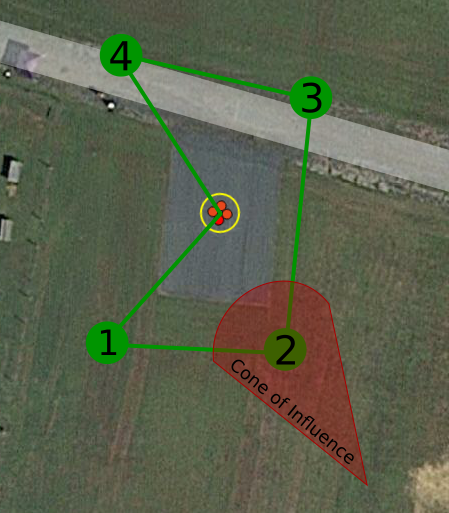
We assume an uncrewed vehicle on a surveillance patrol mission; the mission objectives include aiming an on-board camera at each of a series of fixed waypoints during patrol. While presented here abstractly, both the UAV properties and the mission described here are also indicative of deployments that are of commercial or defense interest.
An attacker with ground station software and a directed antenna sends malicious MAVLink packets repeatedly. The attacker's signal radiates in a cone pattern (shown in red as the Cone of Influence). Upon vehicle entry into the cone of influence, the attacker can send packets that divert the path or heading of the vehicle, preventing capturing of a focused picture of the waypoint. We assume that the attacker is motivated by subtlety and will not seek to simply crash the vehicle or otherwise overtly draw attention. Such an attacker seeks to slightly influence the vehicle, concealing the exact source location of the attack.
We conduct our hardware experiments at Milton Field, which is owned by the University of Virginia.
The flight plan (QGroundControl Waypoint Format) is available here.
Click here to download a Python script for simulating the cone of influence in our attack scenario. When run, the script will protect a sphere of a given radius around a given GPS coordinate. Communication can occur with the MAV either over UDP or an RF telemetry radio (specified at run-time).
We gratefully acknowledge the partial support of the Air Force Research Laboratory (via grant FA8750-15-2-0075). Any opinions, findings and conclusions or recommendations expressed in this material are those of the author(s) and do not necessarily reflect the views of AFRL.
Template by Bootstrapious
Modified by Kevin Angstadt